Cipher-VPN
 The development of information technologies, as well as globalization processes in modern society, form the task of ensuring the transfer of information between geo-distributed computing networks and ensuring privacy for transmitted data over public networks. Often there is a need to ensure private data transfer over the Internet for existing information systems, where it is no longer possible to make changes to performing protection mechanisms. Ensuring privacy when transferring data over the Internet is solved by virtual private network (VPN) technology.
The development of information technologies, as well as globalization processes in modern society, form the task of ensuring the transfer of information between geo-distributed computing networks and ensuring privacy for transmitted data over public networks. Often there is a need to ensure private data transfer over the Internet for existing information systems, where it is no longer possible to make changes to performing protection mechanisms. Ensuring privacy when transferring data over the Internet is solved by virtual private network (VPN) technology.Building a VPN, it is recommended to pay attention to:
-
Flexibility and simplicity of key management.
-
Simplicity of using and integration.
-
Flexibility and convenience of network configuration.
-
Rate of data transfer.
-
Perspectivity (supported algorithms).
-
Orientation on cloud technologies.
-
Wide range of supported hardware platforms and operation systems (OS).

Description
Cryptographic information protection system "Cipher-VPN" is a software or hardware-software complex, based on the OpenVPN protocol with SSL/TLS support to ensure privacy in the time of transferring data in computer networks.
CIPS "Cipher-VPN" allows you to ensure privacy (encryption) between:
-
Network-Network (Server-Server). This approach allows you to build a VPN connection between different networks, where all traffic will be protected.
-
User-Network (Client-Server). This approach allows you to build a VPN connection between the user's computer and the network that is located behind the VPN Server.
Cryptographic algorithms are used to ensure privacy:
-
Implemented in the library of cryptographic primitives "Cipher+" v2.1 (there is a valid positive expert review).
-
Cipher team experience.
CIPS "Cipher-VPN" can build around a public key infrastructure (PKI):
-
Keys published by CA/QTSP. In this case, in order to authorize users to the protected network, can be used:
- Checking the certificate status out using the OCSP protocol.
- Maintaining a list of trusted CAs/QTSP on the VPN server.
- Maintaining a list of allowed users on the VPN server.
-
Keys issued by the internal CA. In this case, the own PKI is deployed using the solutions:
- CIPS “Cipher-X.509” (qualification is possible)
- CIPS “Cipher-xCA” (for internal use)
It is allowed to use as cryptographic algorithms as:
-
National cryptographic algorithms
- DSTU 4145:2002.
- GOST311-95, DSTU 7564:2014.
- GOST 28147-89, DSTU 7624:2014.
-
International cryptographic algorithms
- RSA, ECDSA.
- SHA-1, SHA-2.
- AES, DEA, TDEA.
Keys of users and servers can be stored:
-
As a file - file key container
- PFX/PKCS#12 (CA of Prosecutor General’s Office of Ukraine, Ukraina CA, CA of NationalDepository of Ukraine, CA Oschadbank, and etc.)
- JKS (CA Privatbank).
- Key-6.dat (CA built on the basis of JSC IIT)
- ZS2 (analogue of PFX / PKCS # 12 Ukraine CA, as well as after conversion to Key-6.dat).
-
On a hardware secure key token:
- In passive mode
- Aladdin/SafeNet/Gemalto eToken.
- Avtor SecureToken-337/338.
- Avest AvestKey.
- Efit EfitKey.
- etc.
- In active mode.
- IIT Almaz-1K.
- Avtor SecureToken-337/338.
- Avest AvestKey
- Efit EfitKey.
- In passive mode
CIPS Cipher-VPN supports a wide range of hardware platforms and operation systems.
-
Hardware platforms:
- x86, x86-64 (AES NI, CLMUL, SSE, AVX). Hardware acceleration is supported.
- ARMv6, ARMv7, ARMv8.
-
Operation systems:
- Server: Windows, Linux, FreeBSD.
- Client: Windows, Linux, MacOS.
- Client: Android*, iOS* (of third party developers, interoperability is provided for international cryptographic algorithms).
The convenience of the operation of CIPS "Cipher-VPN" is provided by
-
An advanced VPN Server Management System
-
An advanced VPN Server monitoring system which was built based on agents and extensions for Zabbix v3.0 +.
-
Possibility of the server and clients flexible configuration. The configuration is performed by distributing previously prepared configuration files to clients.
One of the most difficult issues of using a VPN is integration with existing systems with minimal changes:
-
Cipher-VPN provides traffic balancing. In this case, a few VPN Servers work as a single unit and connections from clients are scattered around the less loaded VPN Servers (with the fewest connections).
-
If it is necessary, Cipher-VPN allows you to protect network connections with high bandwidth, due to the aggregation of virtual network interfaces. In this case, the computer system might be loaded in an optimal way.
-
Traffic aggregation is achieved due to the parallel work of several VPN Servers on one computer system. In this case, VPN Servers are bound to different ports and/or addresses.
-
The approaches used in Cipher-VPN to build a VPN Server provide an effective opportunity to work on both physical and virtual equipment.
VPN Server delivery options
-
Docker container. It is recommended for privacy when connecting to cloud resources.
-
Virtual machine. It is recommended for privacy when connecting to cloud resources.
-
Archive with the distribution kit for self-installation.
-
Can be executed in a protected hardware design (pre-order).
The Application Area
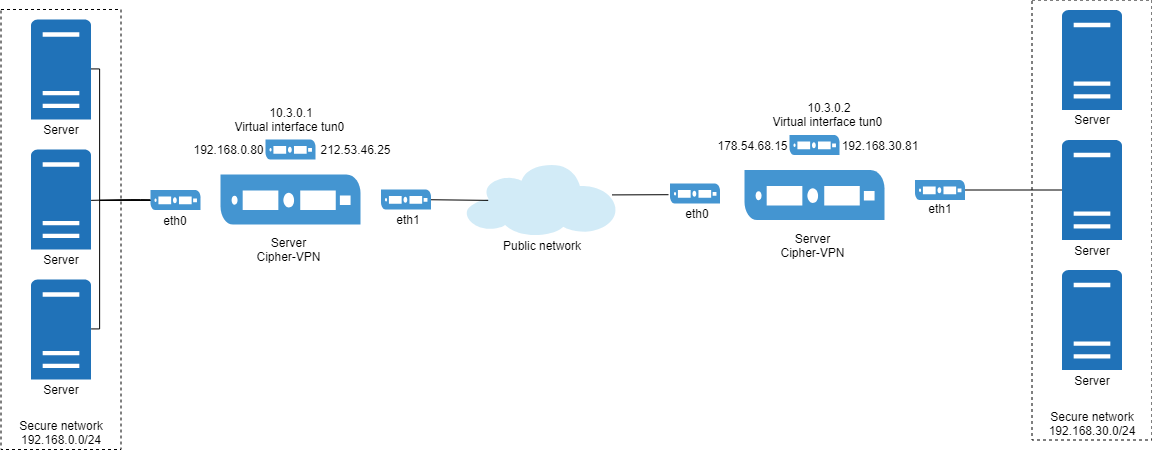
One of the typical tasks that can be successfully solved by the CIPS "Cipher-VPN" is building a secure channel between two networks.
A VPN Server is deployed on both sides, which can:
-
Manage traffic between networks behind VPN.
-
The ability to pass traffic through firewalls and HTTP-proxy.
-
Either encrypt or not encrypt (but tag) traffic.
-
Aggregate traffic from a few network interfaces, and perform the reverse conversion.
-
These servers use static identical keys in PKCS # 12 container.
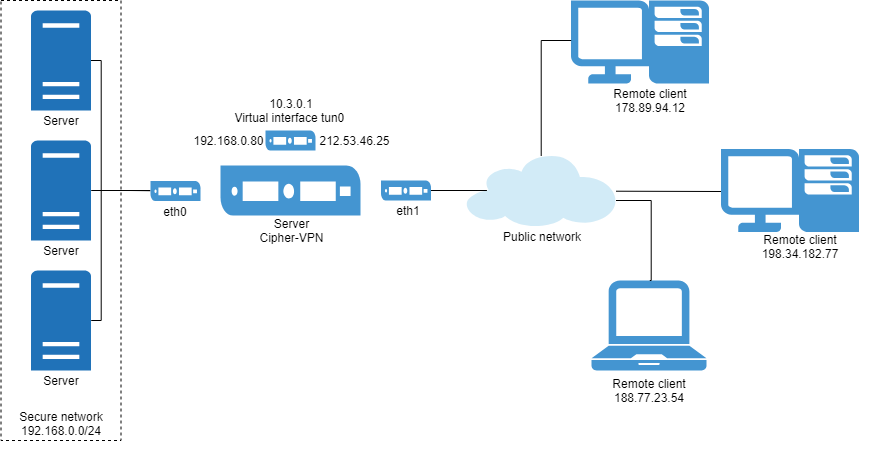
One of the typical tasks that can be successfully solved by the CIPS "Cipher-VPN" is building a secure channel between the user and the network.
On the one hand, a VPN Server is deployed and the user has a VPN Client.
On the VPN Server side:
-
Management of traffic between networks behind the VPN.
-
Passing of traffic through firewalls and HTTP-proxy.
-
Either encryption or not encryption (but tag) of traffic.
-
Aggregation of traffic from multiple network interfaces, and perform the reverse conversion
-
These servers use static identical keys in a PKCS#12 container.
-
Parallel work of several VPN Servers.
-
Balancing connections between a pool of VPN Servers.
-
Various grounds user's authentication
-
Support for working with CA via OCSP over HTTP protocols to check the status of the certificate out.
On the Client’s VPN side:
-
Using configuration files with the configured settings for the intended VPN Server.
-
Connection to a pool of VPN Servers on a rule: "who will be the first to answer"
-
Management traffic between networks behind VPN
-
The ability to pass traffic through firewalls and HTTP-proxy
-
Either encryption or not encryption (but tag) of traffic.
-
To store keys in file key containers and on protected tokens.
-
To store a password in memory to a protected token or require it to be entered several times.
-
Support for working with CA behind the OCSP over HTTP protocol, to check the status of the certificate out.
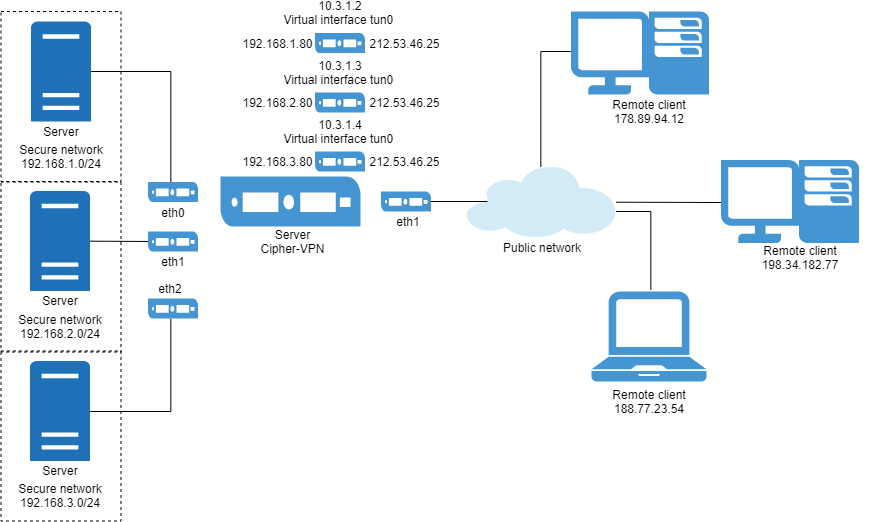
One of the typical tasks that can be solved successfully by the CIPS Cipher-VPN is building a secure channel between the user and the network.
On the one hand, a VPN Server is deployed and the user has a VPN Client.
On the other, on the VPN Server side, it is possible to control traffic from client connections between different networks.
Distinctive Characteristics
There are many approaches to building a VPN, depending on the network layer
-
Network (IP/IPSec).
-
Transport (TCP/UDP).
These approaches have both positive and negative sides.
Among the existing solutions and approaches, there is the OpenVPN protocol with SSL/TLS support, which allows to provide:
-
Firewall, Proxy, NAT transparency is bigger versus LT2P/IPsec.
-
Higher performance with less compute resources than LT2P/IPsec.
-
Support for transport layer protocols TCP, UDP.
-
Compression of traffic using algorithms LZO, ZIP.
-
Flexibility of configuration on the client side by means of pre-installed configuration files.
Runtime Performance
A laboratory install was used in the performance evaluation:
-
One server.
-
Four client’s workstations.
The laboratory install was connected to a local network using a high-performance managed network layer 3 switches.
Below there are the characteristics of the server and client's workstations.
|
Server (physical)
|
Client (physical)
|
|
|
The bandwidth of an encrypted connection without traffic aggregation (one VPN server instance) is shown.
The experiments took into account:
-
The bandwidth with traffic aggregation (a few instances of VPN Server running on one physical server).
-
To reduce the processor load on the physical server side where the VPN Server is running, it is recommended to use processors that support AES NI instructions.
With traffic aggregation
|
Algorithm
|
TCP, Mb/s
|
UDP, Mb/s
|
|
AES-256
|
720
|
920
|
|
GOST 28147-89
|
100
|
200
|
|
DSTU 7624:2014
|
500
|
900
|
The bandwidth is shown in the time of aggregating 4 logical VPN links using 4 processor cores.
No traffic aggregation.
|
Algorithm
|
TCP, Mb/s
|
UDP, Mb/s
|
|
AES-256
|
190
|
290
|
|
GOST 28147-89
|
30
|
55
|
|
DSTU 7624:2014
|
140
|
260
|
Bandwidth is shown per processor core. If it is necessary, the bandwidth can be increased due to the aggregation of virtual links.
Product Documents
CIPS "Crypto-VPN" has a positive expert review of the State Service for Special Communications and Information Protection of Ukraine 12/29/2023 No. 04/05/02-1192/ML1.
CIPS "Crypto-VPN" has a copyright certificate of the Ministry of Economic Development and Trade of Ukraine on 08.04.2019 No. 87538.
CIPS "Cipher-VPN" is built on the basis of the libraries of cryptographic primitives "Cipher+" v2.1, which have a positive expert review of the State Special Communications Service and Information Protection of Ukraine on 08/21/2022 No. 04-1022/ML1.
